- Microsoft has revealed how it protects Azure with an Integrated HSM chip
- Azure security stack includes Azure Boost, Hydra BMC and Caliptra 2.0
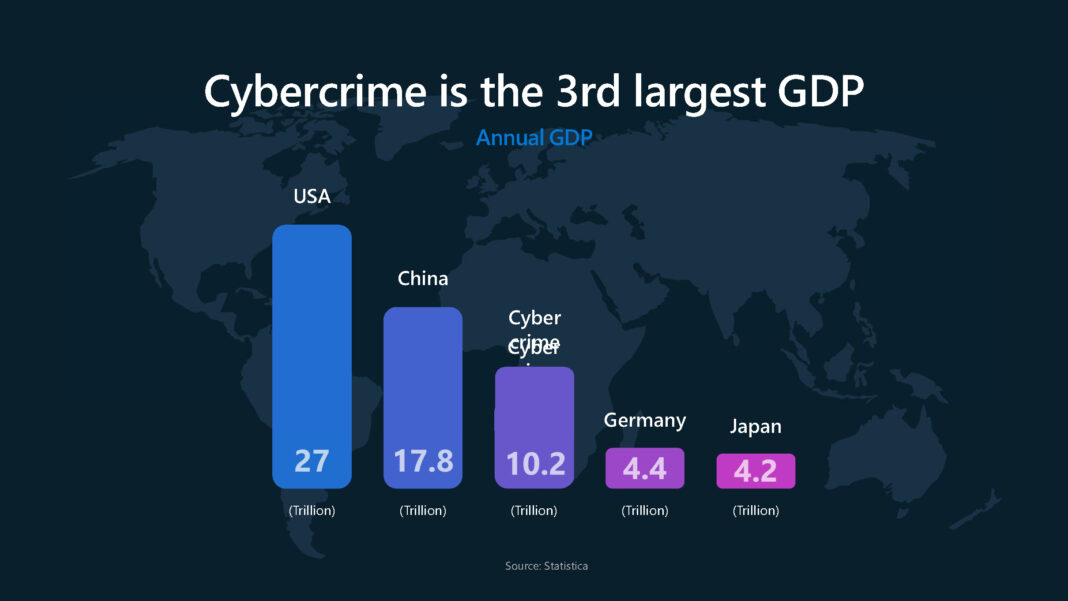
- Cybercrime reportedly worth $10.2 trillion annually, making it the world’s third-largest economy in 2025
Microsoft has revealed more on the custom-built security chip it deploys across every Azure server, aiming to counter what it calls a cybercrime “pandemic” now costing $10 trillion annually.
The Azure Integrated HSM, which was first announced in late 2024, is the centerpiece of a wider security architecture the company outlined at the recent Hot Chips 2025 event.
A slide Microsoft showed there claims the global cost of cybercrime is currently $10.2 trillion - meaning it now ranks as the equivalent of the third-largest economy in the world.
Azure security measures
The trillion-dollar estimate places cybercrime behind the United States and China, but ahead of Germany and Japan, and also far bigger than the entire AI market.
Microsoft said the scale of the threat requires both architectural and operational changes.
As ServeTheHome reports, the company listed a number of statistics at the event, including that Azure already spans more than 70 regions and 400 data centers, supported by 275,000 miles of fiber and 190 network points of presence, along with employing 34,000 engineers dedicated to security.
To take on the cybersecurity problem at a hardware level, Microsoft moved from a centralized hardware security module model to its own Azure Integrated HSM.
The custom ASIC is designed to meet FIPS 140-3 Level 3 requirements, providing tamper resistance and local key protection within servers.
By embedding the chip in each system, cryptographic functions no longer need to pass through a centralized cluster, reducing latency while enabling tasks such as AES, PKE and intrusion detection locally.
ServeTheHome noted building an in-house chip required trade-offs. Instead of scaling hardware security modules at a cluster level, Microsoft had to size them for individual servers.
The result, the company argued, was a balance between performance, efficiency and resilience.
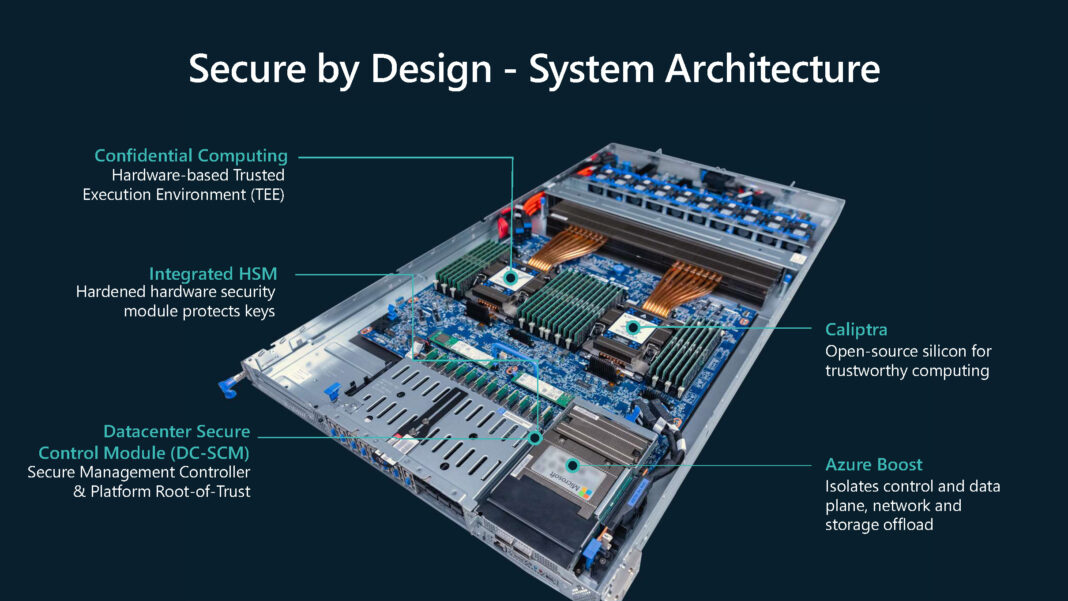
The tech giant also presented its “Secure by Design” architecture at Hot Chips, part of its Secure Future Initiative.
This includes Azure Boost, which offloads control plane services to a dedicated controller and isolates them from customer workloads, and the Datacenter Secure Control Module, which integrates Hydra BMC, and enforces a silicon root of trust on management interfaces.
Confidential computing, backed by trusted execution environments, extends protection to workloads in multi-tenant environments.
Caliptra 2.0, developed in collaboration with AMD, Google and Nvidia, anchors security in silicon and now incorporates post-quantum cryptography through the Adams Bridge project.
You might also like
from Latest from TechRadar US in News,opinion https://ift.tt/ut26Ffd